Structure Your Program
How to Structure Your Cybersecurity Program
Your information security program will be shaped by your organization’s unique needs and business processes. There is no one-size-fits-all solution. The Cybersecurity Framework (CSF), published by the National Institute for Standards and Technology (NIST), is a flexible, adaptable tool for organizing any information security program, regardless of size and resources. Although an institution will never be completely invulnerable, organizing your bank or nonbank cybersecurity program around the NIST CSF supports a comprehensive level of risk management.
The Framework organizes cybersecurity into five core “Functions,” each of which represents a collection of behaviors: Identify, Protect, Detect, Respond, and Recover.
Please note the Federal Financial Institutions Examination Council (FFIEC) provides a mapping of the FFIEC Cybersecurity Assessment Tool (CAT) to the NIST CSF for ease of coordination and communication.
The Identify function helps establish what your organization must protect. Identify activities include determining what assets—both physical and informational—are present within your institution; how they fit in within the business environment; and the governance in place to manage your organization’s regulatory, legal, and risk environments.
All of these activities make up your risk assessment, an evaluation of the threats faced by your institution, the likelihood they will happen, and the magnitude of harm should they occur. The results of your risk assessment will influence the overall risk management strategy, or how you plan to conduct business operations in such a way to limit risk to an acceptable level.
A risk assessment should be performed at least annually to confirm if an organization’s resources, priorities, or business operations have changed significantly enough to warrant a strategy modification.
A cybersecurity risk assessment should classify critical information assets, identify threats and vulnerabilities, and communicate that risk to necessary personnel, including the Board. Before you can adequately assess risk to your institution, though, you must first identify your Crown Jewels, or your most critical information assets. “Crown jewels” are often highly sensitive and guarded and their loss, destruction, or theft could severely impact your institution.
Identifying Threats
To identify potential cybersecurity threats, your financial institution may use internal resources, such as audit reports, vulnerability scans, and fraud detection tools; or external resources, such as information sharing networks like the Financial Services – Information Sharing and Analysis Center (FS-ISAC) and the United States Computer Emergency Readiness Team (US-CERT). A tool like a vulnerability scanner is also commonly used to identify weaknesses by scanning your business environment against well-known and previously identified vulnerabilities. You can also test to determine if an identified vulnerability is actually exploitable.
In November 2014, the Federal Financial Institutions Examination Council (FFIEC) issued a statement recommending that financial institutions of all sizes participate in the FS-ISAC as part of their process to identify, respond to, and mitigate cybersecurity threats and vulnerabilities. Additionally, two publicly available reports that can provide current threat intelligence are Verizon’s Data Breach Investigations Report and Symantec’s Internet Security Threat Report. Both reports are updated annually.
Threat identification should occur continuously throughout the year and not only during the annual risk assessment. When news of a fraud, breach, or other incident emerges, consider whether your organization is also vulnerable. Could the same thing happen to your institution? What controls are in place to help protect against the threat?
FS-ISAC for Financial Institutions
FS-ISAC offers a basic membership for community banks with less than $1 billion in assets which includes the “must-have” services shown below. Nonbanks can also obtain FS-ISAC membership. To receive only the most critical public alerts, the smallest community-based institutions may elect to register as a Critical Notification Only Participant (CNOP). This service is offered free-of-charge but only provides notification of public urgent and crisis alerts. Learn more at https://www.fsisac.com/join.
FS-ISAC’s Services for Community Banks:
- FS-ISAC established the Community Institution Council (CIC) to provide a forum for community banks to share information. All new community banks/credit union members are added to this group.
- FS-ISAC distributes weekly Risk Summary Reports to all community bank members. These reports help explain how the latest risks affect banks and their customers, and how these risks can be mitigated.
- Community Bank FS-ISAC members have access to the FS-ISAC Security Tool Kit, a 72-page document developed collaboratively with community institutions designed to provide a set of security practices to help strengthen banks’ information security programs in light of increasing threats.
- FS-ISAC disseminates actionable threat, vulnerability and incident data to all members.
Measuring Risk
To effectively measure your organization’s level of risk, a method for measuring risk must be developed. One approach is to give each asset a value of high, medium, or low. The rating can be financial but should also factor in how critical the asset is to your business. The risk level of those information assets is also given a rating of high, medium, or low. The final level of risk depends on remediation actions taken by your institution; mitigating controls can reduce the overall level of risk. For example, if backups are routinely performed, the risk posed by the loss of an electronic file may be low.
Confidentiality, Integrity, and Availability (CIA) form the information security triad. Information security programs should be set up to ensure the CIA of all information assets, from data to hardware to networks.
Information Security Triad
- Confidentiality means information is protected from unauthorized access or disclosure.
- Integrity confirms information is trustworthy, accurate, and protected from unauthorized modifications.
- Availability guarantees reliable access to and use of information and information systems.
Communicating Risk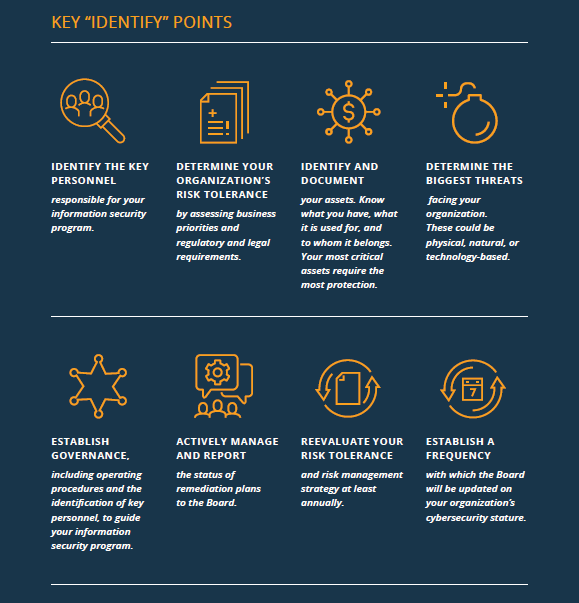
It is vital to establish a process that informs senior management and the Board of Directors about cyber risks to your organization, how your organization currently manages and mitigates those risks, and who is accountable for doing so. Once the risk assessment is developed, adopted, and approved, it should be reviewed and updated at least annually to ensure new risks are identified.
The risk assessment is one element of a larger cyber risk management process that each organization should have in place. CEOs should strive to create and implement an effective and resilient risk-management process that enables proper oversight and ensures effective management of cybersecurity risk. Key elements of a risk management process include the initial assessment of new threats; identifying and prioritizing gaps in current policies, procedures, and controls; and updating and testing policies, procedures, and controls as necessary.
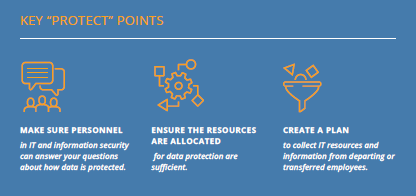
Once institutional threats are identified, the next step is to ensure your financial institution has safeguards commensurate with your risk profile. The Protect function includes establishing physical and information security controls, employee training programs, and operational processes that work to ensure your information and assets remain safe. Protection activities can be physical, such as behavioral processes, or technical, like automated tools.
Incorporate cybersecurity into your human resources and IT acquisitions processes. Planning ahead reduces the likelihood of a catastrophic event occurring, as well as associated mitigation costs. Do not store all crown jewels in one place and ensure backup copies of data are stored in a secure, separate location. For more information on information and business recovery planning, as well as to explore backup agreements with other institutions, please visit Sheltered Harbor.
Sheltered Harbor is an organization dedicated to protecting financial information from permanent loss through the establishment of best practices and a secure backup program for critical institutional customer account data. In the event of a cyber-attack, Sheltered Harbor can transmit a victim institution’s critical data to a partner organization, who will temporarily resume critical financial services until the original provider’s functions are restored.
Malicious actors often gain access to valuable resources due to avoidable human error, so ensure your employee training program includes cybersecurity best practices and social engineering exercises. All attempts should be made to enact the same safeguards and protections at all work locations, including telework and remote locations. Your protection processes should be regularly updated, whenever your business environment changes or if a vendor informs you of an identified weakness. Test the effectiveness of protection tools and processes, whether by internal audits and scanning and/or by engaging the services of a penetration tester.

Another common threat vector is less secured vendors that are given access to your systems. Vendor management should include security reviews of vendors with system access and specify contractual requirements that vendors protect your information at least as well as you do.
The Center for Internet Security (CIS) publishes an annual list of the 20 controls most vital to a robust cybersecurity program. Institutions that effectively incorporate these controls are taking important steps to protect themselves and their consumers. CIS also makes available a Controls Self-Assessment Tool (CSAT) to help institutions determine how effectively the controls are applied.
Cybersecurity Staff Training Resources
- Start a conversation! The Federal Deposit Insurance Corporation’s (FDIC) “Cyber Challenge” encourages community banks to run through and practice their responses to hypothetical cyber scenarios. Find it here.
- The National Cyber Security Alliance (NCSA) website covers safety basics here.
- Check the security of your devices using free tools, made available by the NCSA here.
- Use National Cybersecurity Awareness Month every October to reemphasize your organization’s commitment to proper cyber hygiene. Details available here.
- The Small Business Association (SBA) provides a free training course on cybersecurity for small businesses. It can be accessed here.
Cybersecurity and Human Resources
It is vital to include cybersecurity in your human resources processes.
- New hires should learn their data protection responsibilities on day one
- Maintain and review records of which employees are permitted to access sensitive information
- Track who possesses what assets, like computers, telephones, and printers, and have a plan to collect them from departing employees.
- Create a notification process so the IT department knows to modify, restrict, or delete access when an employee is hired, transferred, out of the office of an extended period of time, or fired.
Useful Protection Tools
- Vulnerability Scanners assess your environment for known vulnerabilities. Many are available for purchase; there are also free tools available online.
- Security Information and Event Management (SIEM) tools log and register activities performed on your systems.
- Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS) alert your IT Team to potential intrusions. Some may even prevent attacks from successfully occurring.
 Hackers will exploit any vulnerability they can find, and it’s up to your IT staff, information security staff, and employees to detect such intrusions. To effectively do this, you must first have a thorough understanding of what is in your asset inventory (see IDENTIFY Section) and how assets are protected (see PROTECT Section).
Hackers will exploit any vulnerability they can find, and it’s up to your IT staff, information security staff, and employees to detect such intrusions. To effectively do this, you must first have a thorough understanding of what is in your asset inventory (see IDENTIFY Section) and how assets are protected (see PROTECT Section).
Your IT and information security staff can then monitor and assess normal business behaviors and look for anomalies. The process is called continuous monitoring, which just means at any point your staff can know what is occurring on your network.
A few common ways to detect intrusions are by using automated tools, like an intrusion detection system (IDS), malware detection tools, data loss prevention tools (DLP) and big data analytics. Other detection methods include independently reviewing records of who accessed what information or facility and following up on anomalies reported by internal users. Engaging the services of a penetration tester, a hacker who tries to gain access to your system (with your advance knowledge) by exploiting unknown vulnerabilities, will also help you determine possible system access points for intruders.
Detecting an incident is less useful if your organization does not know how to respond. An incident response plan is an organized approach to addressing and managing the aftermath of a security breach or attack. The incident response plan should include a policy that defines what constitutes an incident, and it should provide a step-by-step process that should be followed when an incident occurs.
An incident response plan will help your bank to successfully understand, manage, and recover from a cyber-attack. Without it, an organization may not even discover an attack in the first place; or, if the attack is discovered, the institution may not follow good procedures to contain damage, eradicate the attacker’s presence, or recover in a secure fashion.
An incident response plan should address:
- The official incident response team, or personnel with response obligations (often includes high-level executives and the CEO, legal representation, information security and IT personnel, and public relations and communications experts);
- Scenarios your organization considers worthy of investigation and the threshold for declaring an incident;
- The chain of command, including who has the authority to declare an official incident; and
- The severity levels that an incident may be sorted (usually low, moderate, or high).
Incident Response Guide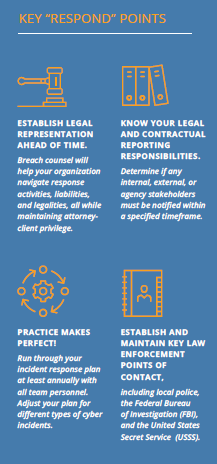
A comprehensive guide on forming and executing an incident response plan is available from NIST.
An incident response plan should include:
- Steps that may be taken to address potential damage and to limit the loss of resources, including any required timelines or Service Level Agreements (SLAs);
- Contractual or regulatory reporting requirements;
- Projected time and resources required to implement the response strategy; and
- A communications plan that incorporates:
- when and if you should report a breach to the media and/or notify affected individuals;
- the preferred medium for notification;
- basic guidelines for tracking and analyzing media coverage; and
- a process for notifying employees of the incident and instructing them about immediate containment steps.
For incident response best practices information on how to form and executive a plan, please refer to:
- NIST Computer Security Incident Handling Guide here; and
- “Cyber Incident Response Guide” published by the Multi-State Information Sharing & Analysis Center here.
Breach Notification
Reporting requirements vary state-by-state and may include federal and international laws in addition to state laws. Please refer to your applicable breach notification law(s), which are available here.
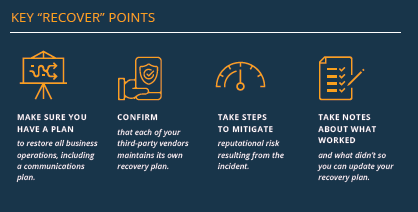
After your institution has taken steps to respond to a cyber incident, the next step is the Recover phase. Recovery includes public relations activities undertaken to mitigate reputational risk, the resolution of internal and stakeholder communications, and the updating of your recovery plans with lessons learned.
By the end of the recovery period, your infrastructure, data, and services should all be restored. This may take anywhere from hours to weeks, but with proper planning it should occur within the predicted timeline.